Proxy Detection: How to Identify Fake IP Addresses
When doing network security or data scraping, it is very important to identify fake IP addresses (i.e. proxy IPs). This not only protects your system from potential fraud, but also ensures that the data you obtain is reliable. This article will introduce some common methods to identify fake IP addresses and help you perform effective proxy detection in the network environment.
1. What is a fake IP address?
A fake IP address usually refers to an IP address that is used to hide the real identity. These IP addresses can be:
Free proxy IP: From a public proxy server, it is usually unreliable and easy to abuse.
Tampered IP address: An IP that has been modified or disguised to cover up the true source.
Fake IP addresses may cause data distortion, network attacks, or security vulnerabilities.
2. How to identify fake IP addresses?
2.1 Check the geographical location of the IP address
Many fake IP addresses come from public proxy servers, which are usually located in uncommon geographical locations. You can use IP geolocation services to check the geographical location of the IP address.
2.2 Use a proxy detection service
Many online services provide dedicated proxy detection functions, which can help you automatically identify proxy IP addresses.
2.3 Analyze the behavior patterns of IP addresses
Fake IP addresses often show abnormal behavior patterns,
High frequency access: a large number of requests are initiated in a short period of time.
The source of abnormal requests: from uncommon or newly registered IP addresses.
By analyzing access logs, you can detect these abnormal behaviors and identify potential fake IP addresses.
2.4 Check the reputation of IP addresses
Some tools and services provide IP address reputation scores, which are based on the historical behavior of IP addresses and reported security issues.
You can use ipinfo.io for detection
IPinfo is a comprehensive IP address data platform that provides detailed information and analysis functions about IP addresses. It allows users to quickly query data such as the geographic location, ISP (Internet Service Provider), and organizational information of IP addresses. Through its intuitive interface and powerful API, identify and prevent potential IP authenticity.
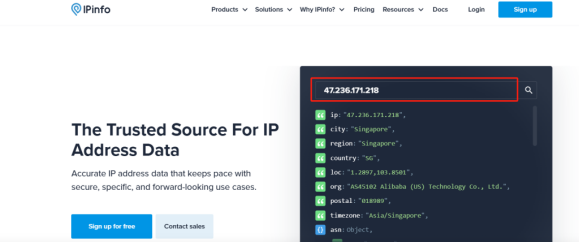
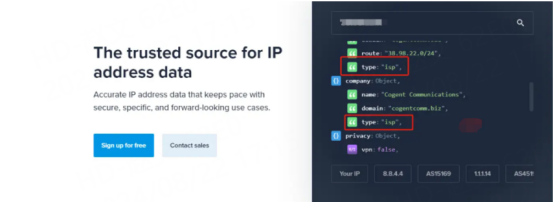
Enter the obtained IP address into the detection column, and find the type column in the inspection report. If the type shows isp, it means that the IP is a residential IP, and the type is hosting, it means that the IP is a computer room IP.
2.5 Usage behavior analysis
Fake IP addresses can be identified by analyzing user behavior such as access patterns, login frequency, etc. Fake IP addresses tend to behave very differently than normal users,
For example:
Abnormal access pattern: Access speed is abnormally fast or access frequency is too high.
Unusual behavior: Such as unusual browsing paths or actions.
3.Why proxy detection can identify fake IP addresses
IP address characteristics: Fake IP addresses usually come from known public proxy services with specific IP ranges. Detection tools can query these IP ranges to identify whether they are proxy IPs.
Geographic location analysis: Fake IPs are often located in data centers or cloud servers, and their geographical location does not match the actual user location. Through geolocation queries, abnormal IP addresses can be identified.
Abnormal behavior patterns: IP addresses using proxies may exhibit abnormal behavior patterns, such as high request frequency or inconsistent access paths. Detection tools analyze these abnormal behaviors to help identify proxy IPs.
Reputation score: Proxy detection services provide IP address reputation scores, and low reputations are usually identified as fake IPs. These scores are based on the IP's historical behavior and reported security issues
4. Conclusion Identifying fake IP addresses is an important part of protecting network security and ensuring data quality. By combining geolocation checks, proxy detection services, behavioral analysis, and reputation scoring, you can effectively identify and deal with fake IP addresses.







































