Linux Operation Guide for Using cURL to Configure SOCKS5 Proxy
In Linux system, cURL is a commonly used command line tool for sending network requests. Combined with SOCKS5 proxy, cURL can achieve higher network privacy and access flexibility, suitable for various application scenarios that need to bypass restrictions or protect privacy. This article will introduce in depth how to use cURL to configure SOCKS5 proxy in Linux, helping users to easily master this practical skill.
1. Why choose SOCKS5 proxy?
When configuring cURL proxy, SOCKS5 proxy is an excellent choice, mainly with the following advantages:
Support multiple protocols: SOCKS5 proxy supports TCP and UDP protocols, and has a wider range of applications.
Privacy protection: SOCKS5 proxy does not record the source IP address when transmitting data, which can better protect user privacy.
Bypassing geographic restrictions: Using SOCKS5 proxy can access resources in a specific region, which is suitable for cross-border access and bypassing network blockades.
By configuring cURL's SOCKS5 proxy, users can implement privacy-protected network request operations while improving the flexibility of network access.
2. Basic knowledge of cURL and SOCKS5 proxy
2.1 What is cURL?
cURL is an open source command line tool that supports sending requests through multiple protocols such as HTTP, HTTPS, and FTP in Linux systems. cURL is suitable for tasks such as data crawling, interface testing, and batch requests. Users can implement powerful network request operations through simple command line input.
2.2 What is SOCKS5 proxy?
SOCKS5 is a proxy protocol that does not record the IP address of the data source, so it is widely used in privacy protection and cross-regional access. Compared with HTTP proxy, SOCKS5 proxy supports higher anonymity and has strong compatibility, which is suitable for use with network tools such as cURL.
3. Steps to configure cURL to use SOCKS5 proxy
In Linux, cURL can use SOCKS5 proxy for network requests through simple configuration. The following are detailed step-by-step instructions.
3.1 Check if cURL is installed
First, make sure cURL is installed in the system. You can check by entering the following command in the terminal:

If it is not installed, you can install it with the following command:

3.2 Choose a suitable SOCKS5 proxy server
To use cURL's SOCKS5 proxy, you first need the IP address and port of a SOCKS5 proxy server. You can get a SOCKS5 proxy in the following two ways:
Self-built proxy server: You can use software such as Shadowsocks to build a SOCKS5 proxy on the server.
Third-party proxy service: Many proxy services provide SOCKS5 proxy nodes, and users can choose paid or free services.
Suppose the obtained SOCKS5 proxy server information is as follows:
IP address: 127.0.0.1
Port number: 1080
3.3 Configure cURL to use SOCKS5 proxy
Configuring SOCKS5 proxy in cURL is very simple, just use the --socks5 parameter. The following is the basic configuration command:
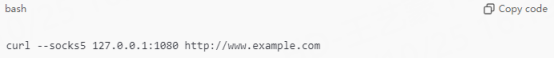
In this command:
--socks5: specifies that cURL uses the SOCKS5 proxy protocol.
127.0.0.1:1080: IP address and port of SOCKS5 proxy.
http://www.example.com: Target URL to be accessed.
With this command, cURL will send network requests through SOCKS5 proxy to achieve proxy access.
3.4 Using SOCKS5 proxy with authentication
Some SOCKS5 proxy servers require identity authentication. Users can specify username and password through the --socks5-user and --socks5-pass parameters. For example:
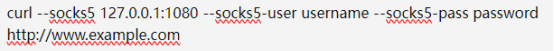
The above command is applicable to SOCKS5 proxy that requires authentication. After providing username and password, it can be accessed normally.
4. Application scenarios of using SOCKS5 proxy in Linux environment
4.1 Improving the privacy of data crawling
In data crawling, directly using local IP may lead to limited access frequency or privacy leakage. By configuring SOCKS5 proxy, cURL can achieve higher anonymity and data privacy protection, which helps to avoid IP blocking or access frequency restrictions.
4.2 Access resources across regions
Some resources are only available in certain regions, and users can use SOCKS5 proxies to access these restricted areas. By selecting the IP address of the proxy server, you can pretend to be a user in another region and easily bypass geographic restrictions.
4.3 Dealing with network restrictions
Some networks may have firewalls or restriction rules that block direct access to certain URLs. Through SOCKS5 proxy, cURL can bypass some network restrictions and access target resources.
5. Notes and FAQs
5.1 Check the stability of the proxy
When using cURL to access resources, the stability of the proxy server is crucial. Connection failure may be due to the unavailability of the proxy server or unstable network. It is recommended to test the availability of the proxy before use to ensure that it works properly.
5.2 Beware of the risks of free proxies
Free proxy servers usually carry higher risks and may have problems such as data leakage or instability. It is recommended to choose SOCKS5 proxies provided by reputable proxy service providers to ensure data privacy and network security.
5.3 Update proxy information regularly
The information of the proxy server may change at any time, including the IP address or port. To ensure the normal operation of cURL requests, users should update proxy information in a timely manner to avoid request failures due to expired proxies.
6. Best practices for using proxies - regularly changing proxy IPs
In order to avoid blocking or access frequency restrictions caused by frequent access to a single IP, it is recommended to change proxy IPs regularly. For example, you can use a proxy pool to dynamically change the proxy IP for each request to improve access stability.
7. Conclusion
Through the introduction of this article, I believe you have learned how to use cURL to configure SOCKS5 proxy in Linux system. Configuring a proxy can not only improve network privacy and access flexibility, but also help realize advanced functions such as data crawling and cross-regional access. In practice, users can adjust the proxy configuration according to specific needs and flexibly use SOCKS5 proxy to optimize cURL requests in Linux environment.

















































